Networkshop Introduction
download ova
virtual box
extension pack
The Linux Infrastructure
kernal is the most prolific.
most used operating system
in the metro, goolge and facebook would not exist without linux
we can extend what we can do with computers, without even an interface
your computational surface
like raspberry pie
universal
with usb ports
communicate with a machine around the world
roll out your own server
log into a machine and configure a website
access it remotely without this desktop landscape
configuring our networks
working in the local ethernet
not on the internet
settings network bridged adapter en0ethernet
randomize media access control
bump the video display to 64
command F (fullscreen)
intensive lesson in the linux command line
the demand for it is heavy still
drones, nuclear submarines, small devices that only use command line
what is a terminal?
as regards to remote machines
a graphical windowing program that hosts a shell (the operational context)
the terminal is what hosts the shell
the promt user@host: ~$
(identity part) host is the name of the machine
~ shortcut for /home/user
$ which level of user
pwd
present working directory
returns the standard output
/home/user (this is the path)
ls
list (turns the lights on)
replies with a lot of directories
desktop documents downloads music pictures public
templates videos (doors to other rooms)
ls D + tab (is a shortcut to what is possible (in this case it is documents/downloads)
ctrl L (shortcut to clear)
~/Desktop$ pwd
replies /home/user/Desktop
touch list1.txt
(puts a.txt on the desktop)
du list1.txt
replies it has 0 size
echo "lalala"
replies lalala
redirect it and put it in the file
use up arrow to repeat the prompts you have already used
so repeats
echo "lalala" > list1.txt
cat list1.txt (dumps the contents of echo into the file)
us of >> keeps the echo from overwriting the cat into the .txt
echo "nanana" >> list1.txt
mkdir archived
make directory (creates a folder on the desktop called archived)
mv list1.txt archived/
move list1.txt to the archived folder (the slash is like a physical indication that you are moving it forward)
cd archived
ls
cp list1.txt list1_backup.txt
ls
replies list1_backup.txt list1.txt
diff list1.txt list1_backup.txt
echo "1,2,3" >> list1.txt
diff list1.txt list1_backup.txt
replies 3d2
rm list1_backup.txt
ls
replies list1.txt
mv list1.txt list.txt
ls
cd …
cd -
(cd back)
cd ~
(to go home)
alles a shortcut for cd/home/user
mv archived irrelevant
renamed the folder to be irrelevant
rm irrelevant
cannot remove, you must add a switch - r (recursion, nested state of an object)
rm - r irrelevant
rm - rf /
recursively and force (major eating of itself)
ls plus a switch called - l
ls -l ..
long listing
mkdir -p 1/2/3/4/5/6/7/8/9
rm -r 1/2/3/
ls 1/2/^C
mkdir -p q/w/e/r/t/y
rm -r [0-9]
rm -r [0-9]*
that begins with the number, regardless of what follows
mv [a-z]* 100/
cd …/Documents/
ls
evince CLI-Cheatsheet.pdf
less copyright
/SOFTWARE
searches for every instance of the word
Q to quit
grep SOFTWARE copyright (file on the desktop)
grep - n
grep -ni software copyright
- o only show me the match
man grep
lists command line
File Systems
bin
boot
dev
ect
/home/user/ruby/desktop/documents…
/johnny/desktop/documents…
lib
usr
var/log
/www/htdocs/
conf
ls /ect/network/i
interfaces defines how your computer is connected to the network
network interfaces
ls/var/
ls /bin
Superuser
someone who can act on the file system
root and superuser is the same thing
SUDO
super user do
root file
sudo touch /foo
DEV
devices:
ex. CPU, memory, sound card
ls /dev/input
ls /proc/
How files connect to hardware.
How computer networks are put together and organized
Stack
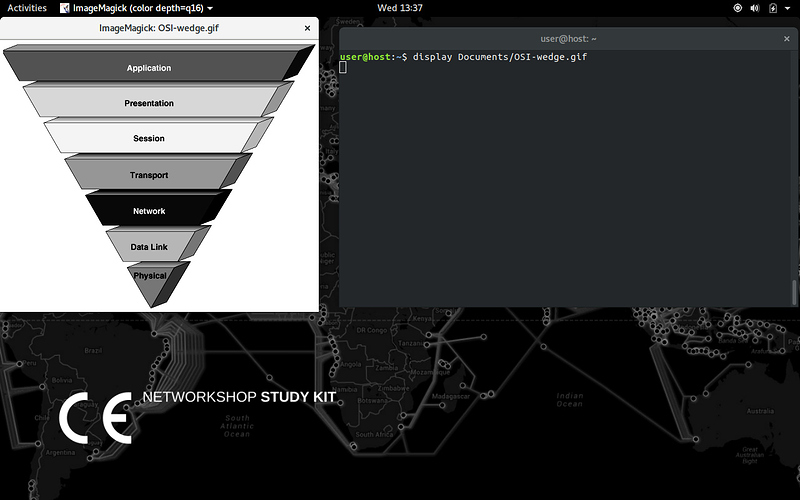
display Document/OSI - wedge.gif
Layers:
Network Stack
4Application
3Protocol
2Netweork Link
1Physical
ifconfig -a
built in ethernet or dongle
-a all available interfaces
eth0:
ether wired connection
ether 08:00:27:69:02:35 fingerprint
MAC media access control
RX received
TX
agree upon a range; sequence of addresses to be used
read from rt to left
192.168.0.1
number on your subnet machine, the number of the subnet itself,
1.0.0.1.
254.254.254.254
network range is defined by the first three numbers
share the same subnet
192.168.1.1
192.168.1.7 (up to 256) able 1
192.168.2.1
192.168.2.7 table 2
imagine from rt to lf the numbers represent: name, house number, address, country
in a star or tree topology
computers connected to a central point
this point is called a router or a gateway (it can communicate to a neighboring network)
via a central host (a device that has an ip address assigned to it)
192.168 (local ip networks)
can be written in 1s and 0s up to 256
sudo ifconfig eth0 192.168.2.1
ifconfig eth0
netmask with a 0 at the end means you are able to communicate with anyone from 0 to 254
inet ip address
inet6
rx packets
man ping
manual ping
ctrl c to escape
packet loss is no bueno as it means its overloaded or somehting is off
Ports and Protocol
data link and network layers need to be linked
you’ve assigned an ip to a physical device
media access controller is a unique fingerprint
static part: mac adress
slippery part: ip addresses assigned
macchanger -l
list all mac addresses
arp
address resolution protocol
who has packets
packet capture
who has this ip
sudo arp-scan -l
link and network link to arp
Require ports
Computer&phone
Lots of little doors, in an open or closed or listening state
Works with a port number given to it
Port #80
443
secure socket layer (ssl)
sudo netstat -tupa
xterm
sudo netstat -tupan
ssh - 22
these numbers are the doors on our systems
creating a new service
net is cat for networks (dumps data into a network)
2way pipe:
must be above 1000 (reserved space for these ports)
nc -l -p 3333
-p for port
The reply is to enter nc plus the Ip of the person plus the port number
ex. nc 192.168.1.128 1234
sudo netstat -tupan
client server relationship.
ctl c to close the connection
file sharing
ls
nc -l -p 333 < a-file.txt (< sends into the stream)
nc -l -p 333 > Desktop/another-file.txt (> sends it to the desktop?)
Interacting with computers elsewhere
getting info remotely
ssh stands for shell (invokes an encrypted tunnel btwn our host)
ssh user@192.168.2.4
ifconfig eth0
sudo reboot -n
exit gets you out of your host and back to your own
ssh user@192.168.2.2 "ls Desktop"
looks in on the desktop and then logs out again right away
insert a space before the prompt and it will be anonymous
ssh port 22 on servers
you can configure a different port
ssh --help
scp (secure copy)
scp another-file.gif user@192.168.2.3:Desktop/
:./or :~/ (both mean drop it into the home dir and can be used in place of Desktop/
cd Desktop/
in blue replies ~/Desktop
scp user@192.168.2.4:Desktop/File.txt .
( . to where i already am)
scp -r user@192.168.2.4:Desktop .
reverse send
direct drop box
weil dropbox is going over 20 machines and then back again, even if you are right next to each other.
1gigabyte of data is equivalent to 26.7 kilos of carbon
every computer can be servers&clients
changing passwords
passwd
apg uses randomly generated phonemes from linguists
Type old password
type new password 2x
sudo adduser
creating another user account without superuser privledges
Joining 2 networks
Router (multi-home hosts)
the other network < two network interfaces > 1 network
1.0 Switch < 1.1 Router 2.1 > Switch 2.0
ping 192.168.1.1
sudo route -n
Kernel IP Routing table
1.0 (because its the network we are arranged in)
sudo route add default gw 192.168.1.1
now we pour ourselves into 1.1 which is the router connecting the two switches.
now when you run sudo route -n
you should still see subnet going to 1.0 (original)
with the gateway 1.1
now you can ping to another alien network which is connected to the router
sudo sysctl -a | grep forward
(has an api with the kernel)
sudo szsctl net.ipv4.ip_forward=0 (no longer able to ping
sudo szsctl net.ipv4.ip_forward=1 (pinging enabled)
sudo arp
sudo arp - n
list ips (only from your local network)
ping -s 6500
(btwn 1-6500, increses the siye of your ping)
Traceroute 192.163.1.3 -n
Traceroute -n
You can see the number of hosts, consumption of electricity (how expensive it is)
Tower stations transporting the electricity, submarine cable routes, think of it as an environmental rating.
24.August.2017 Day 2
Packets
network packet
forensic analysis software
take the concept of a File:
there is a Header (INFO, rgb/a, html) and they have a body (where the DATA is, pixel data, Content, the packets Payload,)
Header
Four different fields:
Src (source address)
Dst (where the packet is going)
Len (length, allocate memory for that packet)
Sn (sequence number: which packet it is to be joined in a stream and in which order ex. 1001…1301)
TCP/iP slower but error free
UDP (for streaming ) where time is critical
4443 SSL
string will be built around the ssl
packets contain encrypted content decrypted on the other end
Ether net frame contains the source of DST
Review about setting up the network:
ifconfig
sudo route ifconfig 192.168.1.1 (to connect to the shared network
sudo route add default gw 192.168.1.128 (to determine your own number within that network)
ping 192.168.1.254
nmap
ifconfig
sudo nmap -sP 192.168.2.*
shows who shares your network, hostname…
Portscan
sudo nmap -T 0 192.168.2.3
Program to use for analyzing packets: Wireshark
sudo wireshark
Frames (like film stills)
Ethernet link layer - what kind of packet, broadcast (in html), source (actual mac address)
DHCP broadcasting on layer 2, link layer establishment below the network layer
User Datagram Protocol (UDP) - uses bootstrap protocol inside
Ping in destination under ethernet mac addresses. no packet info, no sequence number in the net packet because its not a stream
TCP packet - seq number 1, corrects to 1439.
http - port 80, seq 2215, response 2216, unzipped reveals the site.
Relationship to the Stack Triangle
frame layer - physical layer
ethernet - link layer
internet protocol - protocol
data - app
Packet Capture
sudo tcpdump -AXvvn -i eth0
-A for asci, X for hex, v for verbose…
Proto ICMP - used by ping and traceroute
Ethernet Tap
the BCSQ and NSA
interception diving and slicing and tapping of submarine cables swapping out hardisks, copies and sends. captures and records everything. Ghosting: you can play it back as if it’s happening in real time.
sudo macchanger -A eth0
changes the mac address so you appear as a bot?
DHCP
with the phone shows up a broadcast request to see if it gets an answer, the router
ARP scan
who at ip address is at mac address
sudo macchanger -A eth0
change mac address
disable and enable card with down and up
with prompt
insert image router overlays here
configure its local internet address so they appear that the router itself is making those requests. router will act as a proxy
third interface on the router eth2
send the broadcast, reaches server/router and responds with an IP address
sudo dhclient eth2 -v
ping 8.8.8.8 (outside ip to test and see) if
sudo route -n (shows the router)
configuring a machine to act as a router:
sudo iptables -t nat -A POSTROUTING -o eth2 -j MASQUERADE
DNS Lookup
| hostname | IP Address |
|---|---|
| google.com | 8.8.8.8 |
local lookup table
cat /etc/hosts
change name of the host machines:
sudo nano /etc/hosts
dont change the local host.
make the name change of the other and hit ctrl o to save the change.
ctrl x to escape out
sudo nano /ect/hostname
change name here as well
sudo hostname (insert name)
it will complain but you should close the terminal and then open a new terminal
restart with small dns system connected to their router
`sudo nano /etc/resolv.conf``
check/change IP Address
sudo systemctl stop system-resolved.service
this enables the ping to outside of the network
sudo driftnet -i eth0
views whats going through the network?
ssh user@javier
? sending things…
ls -l /var/www
ls -l /var/www/html/
cat /etc/group
priviledged escalation
sudo addgroup user www-data
cat /etc/group | grep www
responds: user
sudo chown -R www-data:www-data /var/www/html
ls -l /var/www/html
replies with:
user, group, all other users
chmod -R ug+rw /var/www/html
users and groups and read and write
ls -l /var/www/html
sudo su - user
touch /var/www/html/test
rm test
moving files
mv index.lighttpd.html index.lighttpd.html_BUP
ls
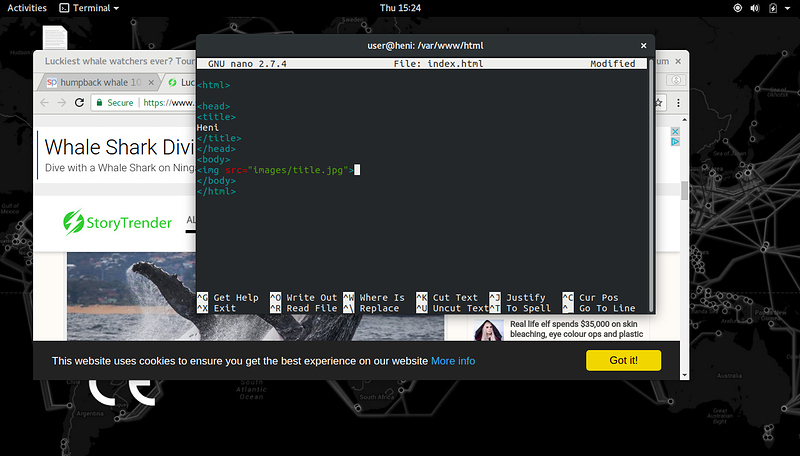
mkdir images
ls
look up an image and rt click, copy image address
cd images/
wget (rt click and paste the copied image address)
mv (repeat image address) (enter a title).jpg (the desired title).jpg
ls
identify title.jpg
to check the size of the images
convert -resize 1024 title.jpg title_1024.jpg
Create a Website
nano index html
to go inside and write these:
TAGS
netstat -tupa
in chromium - http://heni
Spoofing
download theintercept to our www dir
wget -r --level=5 https://theintercept.com
recursively download pages should they be linked
recreate a file link with a site
point the server to the new dir
sudo nano /etc/lighttpd/lighttpd.conf
in nano under “server.documenert-root”, change the website address
sudo service lighttpd restart ?
sudo service dnsmasq restart
assign and add the website address.com to an IP Address
generate a certificate on your own domain, adding a bit of characters and phish for your password
https://null-byte.wonderhowto.com/how to/defeat-ssl-practice-with-ssd-strip.0130260
Wifi
802.11b/g ==2.4>2.5GHz
same domain as a microwave
overloaded so
802.11a ==5 GHz was created
using wifi hardware, airport, higher up the spektrum, shorter wavelength, higher bandwidth, the possibility of more information faster
wifi
radio frequency hardware
a switch
router
scan your wireless environment
find what is not being used and use it
radio link is established by frequency or channel
passphrase
then you drop to the networking stack
access points
sudo ifconfig -a
sudo ifconfig wlan0 up
airmon -ng start wlan0
access points in the area
sudo airodump -ng wlan0mon -c 1 -t WPA -w weise1
individual stations
bssid unique mac address base station
channel 1 radio (out of the box wlan box)
man airodump-ng
Modes
adhoc mode push data to each other
monitor mode
listening mode
manage mode
#data column
number increases if someone is downloading something
you can capture it -w (plus the name of the ESSID you want to capture)
sudo drift ^c
dec.cap (de-encapsulated)
rt click
follow–>tcp stream
save out as ASCII
in terminal check for that saved image
du -h img.jpg
vim img.jpg
jfif is the header of jpeg
Connecting with USB Stick
sudo iwlist wlan0 scan
sudo iwconfig wlan0 essid CE_intensives
to make the radio link
sudo dhclient -v wlan0
asking for an ip
sudo route -n
sudo airodump-ng wlan0 -t OPN
sudo iw list
give you info about the dongle
sudo iwconfig wlan0 mode Managed
a mode which receives all the traffic
sudo iw list | less
lists the modes
sudo airmon-ng start wlan0
run a virtual maschine at the same time.
with the virtual, you can manage
sudo iwconfig wlano mode Monitor
sudo iwconfig wlan0
25.August.2017
man airodump -ng
to view the manual
Connecting the wlan with antenna review
select device (bottom rt hand side)
sudo ifconfig -a
sudo ifconfig wlan0 up
Sets it in Monitor mode
sudo airodump-ng wlan0
sudo airodump-ng wlan0 -t OPN
Runs the possible networks (unencrypted) ssid of the network channel, pwr, beacons, data…
use the airdodump command to see which channels are less congested
Spacebar to pause, tab to get selection key
sudo airodump-ng wlan0 -c Quits mkdir captures cd captures $captures run sudo airodump-ng wlan0 -c 8 --bssid 02:90:4C:C0:00:01 -w BVGCaptures Watching the data capture: watchdu -h bvg-01.cap ls du -h bvg-01.cap ls -lh(size of files)airdecap-ng bvg-03.cap mk dir flows cd flows/ tcpflow -r …/bvg-03-dec.capread, work with directory abovelspresents a log of ip to ip addresses **extracting data from these files:**foremost -i ..*`
files–>captures–>flows–>output–>
wireshark–>open file
airdecap-ngc (name of file.cap)
ex. airdecap-ng BUCKWEATS-01.cap
Wpa (encrypted)
OPN open
Browser pop up is fine, to capture open wireless traffic.
bumping off networks
sudo^C
sudo iwconfig
run airodump to check the client
sudo aireplay-ng -a (bssid identity) -c (client station) -0 20 wlan0
a is access point bssid, c is client station, zero is a switch number that follows is number of packets and the network
client station to bump off
sudo iwconfig wlan0 channel 8
locked onto channel 8
airodump-ng -b a wlan0
installing vpn with command line
traceroute instagram.com
traces all the computers going through to insta
vpn has encryption along the route
vpnbook.com
open vpn tab, right click, save link as…
download vpnbook
cd Downloads/
ls
unzip VP tab
copy pass on vpn
sudo openvpn vpnbook-us2-tcp80.ovpn
client
pass paste
sudo apt-get install openvpn
username
pass
vpnbook
password
initialized sequence completed!
tun device
go to browswer
recheck wtfismyip
privacy until the vpn server
cat /etc/resolv.conf
to check your dns info
sudo nano /etc/resolv.conf
to change the nameserver and ip 8.8.8.8
use the dns of the country or not of the home
write out
opendns.com can give you an ip
vpnschufing?
yougetsignal.com
install nextcloud, vpn on phone and computer, get to files from the mobile device. or better yet, set up your own vpn server.